As embedded devices contain some kind of programmable processor by definition, they are products with digital elements and must comply with the Cyber Resilience Act (CRA). The more interesting question is if they are default, important or critical products. Manufacturers have an understandable tendency to declare their devices as default products or to avoid the CRA altogether. I will clarify the classification by examples.
Air Velocity Meter
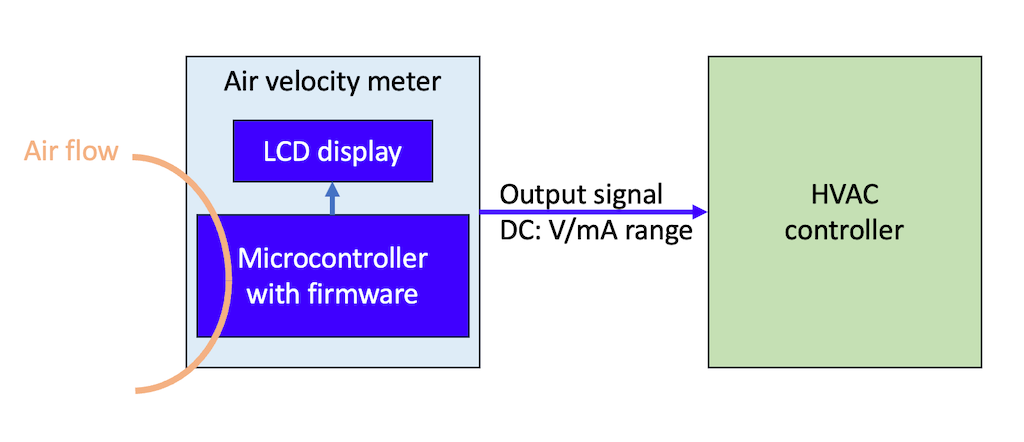
The air velocity meter measures the speed of air. Firmware on a microcontroller takes continuous measurements and outputs them as an analogue voltage (V) or current signal (mA), which is linearly related to the speed. The meter sends the speed to an HVAC controller to control the through fresh-air and exhaust-air ducts. The meter also displays the air speed on an LCD display.
The manufacturer flashes the firmware on the meter once during production. The firmware never changes during the entire lifetime of the device. If the meter reaches its end of life after 20, 30 or more years, it is replaced with a new one. Repairing wouldn't be worth it.
The manufacturer concluded that the air velocity meter doesn't fall under the CRA. They reasoned that they install the firmware on the microcontroller before they place the meter on the market and that nobody can change the firmware during the entire lifetime of the meter. Article 2.1 refutes their argument.
[The CRA] applies to products with digital elements [whose] intended purpose or reasonably foreseeable use [...] includes a direct or indirect logical or physical data connection to a device or network.
CRA, Article 2.1, Scope
The air velocity meter contains - without doubt - digital elements: the firmware running on the microcontroller. It also has a direct physical connection to devices in the network of the HVAC controller. The meter is certainly in the scope of the CRA. The manufacturer must perform the necessary compliance for meters placed on the market after 11 December 2027.
As the firmware never changes: How on earth could attackers manipulate the measurements!? Attackers could inject malicious code into the firmware before it is flashed on the device. This is known as a supply-chain attack. NotPetya and SolarWinds are notable examples of such attacks.
Would the meter still fall under CRA, if we removed the output port? Yes, it would. The direct physical connection would become an indirect logical connection. A human operator would have to look at the display of the meter and decide how to change the flow through the air ducts. The attack vector would be the same.
The manufacturer could delay CRA compliance for some time, because the meters don't undergo any substantial modifications after being sold. They could produce a huge batch of meters, create a distribution company (a distributor in CRA speak) and sell the batch to the distributor before 11 December 2027. Article 69.2 exempts them from CRA compliance for this batch.
The intended purpose and the reasonably foreseeable use, as stated in the operation instructions, decides whether the meter is a default, important or critical product. The meters are intended for use in ventilation or air-conditioning systems. They must not be used for measuring inflammable or aggressive gases.
The meters must not be used in critical infrastructure. If they were manipulated, the implication could be some unpleasant noises and some extra friction in the air ducts. But, it wouldn't harm people. This rules out critical and important products and turns air velocity meters into default products.
We have learned that the intended purpose and reasonably foreseeable use have a strong impact on the CRA classification. Our natural instinct is to define them as narrow as possible. However, "reasonably foreseeable" prevents us from going overboard with excluding too many uses.
