The Question for Sleepless Nights
If you think that the CRA does not hold for products sold before 11 December 2027, you are wrong. The CRA holds for such legacy products, if they receive feature updates after that date. These products must undergo full CRA compliance.
CRA compliance is not about producing a paper tiger, but about implementing concrete security measures. The CRA requires you, the manufacturer, to raise the cybersecurity level of all your products to the state of the art. CRA compliance is a lot of work for one product, let alone for multiple products.
Given the limited time and the considerable efforts, you'll probably start asking the following two questions.
I cannot answer the second question, because this is your business decision. However, I can help you answer the first question, which will facilitate your business decision. After finishing the CRA Survival Bootcamp, you will have a rough plan which security measures need implementing and a fairly good idea about the effort.
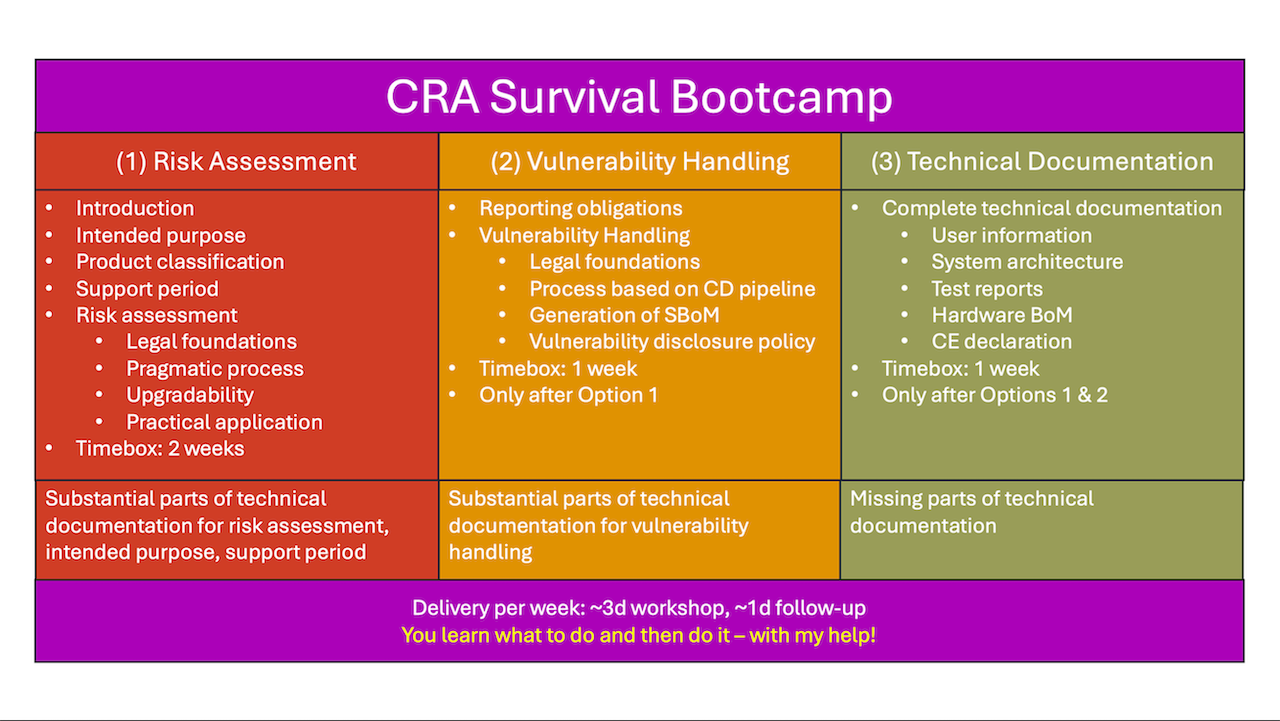
- Step 1 - Risk assessment (Annex I.I). With a pragmatic risk assessment process, you identify a fairly minimum set of security measures that is just enough to satisfy the essential product requirements. You document the risk assessment with architecture decision records for verbatim inclusion into the technical documentation. Risk assessment is the centrepiece of CRA compliance.
- Step 2 - Vulnerability handling (Annex I.II). You define a vulnerability handling process that enables you to filter out the few relevant from hundreds of vulnerabilities quickly and safely. The vulnerabilities come from three sources: from vulnerability databases for third-party components, from your own penetration testing and from user reports. The selection of the right vulnerability handling tool is essential.
- Step 3 - Technical Documentation (Annex VII). The rest is paperwork. Fortunately, steps 1 and 2 cover large parts of the technical documentation. Step 3 adds the missing information.
In the post Surviving the Cyber Resilience Act, you find more details how you can perform CRA compliance with reasonable effort.
The CRA Survival Bootcamp in a Nutshell
The CRA Survival Bootcamp targets manufacturers of embedded systems. Target systems include agricultural, construction, packaging, weighing or vending machines, measurement instruments and commercial appliances. They also include machine components like ECUs, telematics units, operator terminals, cameras, boards, SoMs and sensors.
In the bootcamp, you'll learn what requirements the Cyber Resilience Act (CRA) puts on you as a manufacturer and how to satisfy these requirements with reasonable effort. Under my guidance, you'll immediately apply the learned theory to your specific system. The bootcamp delivers three important results:
- a plan for implementing security measures and a vulnerability handling process (including effort estimates),
- the knowledge how to do CRA compliance on your own, and
- substantial parts of the technical documentation.
I will personally guide you through the entire bootcamp. For 20+ years, I have been developing embedded systems including infotainment systems for cars, XRF analysers and operator terminals for harvesters, excavators or metal-sheet bending machines. Similar to you, I am approaching cybersecurity from the practical side. We'll work out a way how to do CRA compliance with reasonable effort, because it is simply not your core business.
Here are my contact details to find out more about the CRA Survival Bootcamp.

In response, you'll receive an invitation to a one-hour online meeting to understand your needs.
Delivery Options
You can order all three options together. Alternatively, you can order the options one after the other: first Option 1, then Option 2 and finally Option 3. You can order only the first Option or the first two Options and do the rest on your own. You must pay all ordered options in advance, before the first ordered option starts.
All three options together will cost you between €25,000 and €35,000.
Our contract contains the start date for each ordered option. The dates can only be changed, if both parties agree. Scheduling conflicts may prevent me from accommodating your wishes.
Assuming that you order all three options, I can deliver them with no breaks, one break or two breaks in-between. The following diagram shows the three delivery options.
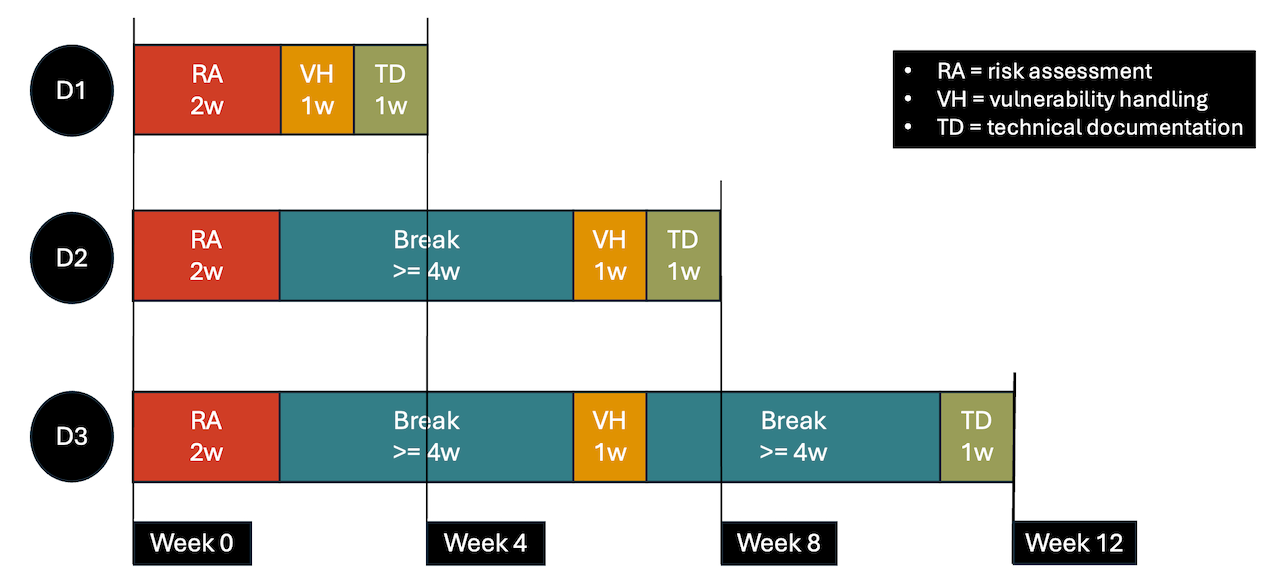
I can deliver the three options consecutively within four calendar weeks (D1). This might be too strenuous for both you and me. We could have a break of at least four weeks between Option 1 and Option 2 (D2). Options 2 and 3 would form one block. The whole bootcamp would take at least eight calendar weeks. We could also have a break of at least four weeks after Option 1 and after Option 2 (D3). The whole bootcamp would take at least twelve weeks.
During the breaks, you can keep me on a retainer for at most six hours per week. You keep working on CRA compliance. I'll be available on demand to answer your questions or review your work. However, you are not obligated to buy a retainer.
The schedule for each week of the bootcamp looks roughly like this:
- You and I work Monday to Thursday on CRA compliance in the bootcamp.
- We spend approximately three days together in workshops. Each of us spends one day on their own with follow-up or preparation work.
- We adapt the workshop and follow-up time on the spot as we see fit.
- On Fridays, everyone is free to do whatever they want.
Questions & Answers
Which CRA product classes are the target for the bootcamp?
Default products. Most embedded systems including agricultural, construction and industrial machines are default products. Nevertheless, default products are neglected by the law and standard makers. A horizontal harmonised standard explaining how to comply with the essential product requirements will become available far too late on 30 October 2027 - six weeks before the CRA applies fully.
Vertical harmonised standards like for important and critical products (due on 30 August 2026) are not feasible for the hundreds of different default products. Vertical standards provide long lists of security criteria that important and critical products must satisfy to achieve conformity. The good news is: Manufacturers of default products get away with much shorter lists of criteria that they can define and assess themselves - within the vague bounds of the CRA. I'll help you identify a minimum set of security measures for your product in the bootcamp.
Who is the target audience?
The members of your security team who will perform the CRA conformity assessment. The security team includes technical people like security engineers, senior software engineers and architects and business people like CTOs, VPs and product owners/managers.
Evaluating the risks and deciding what to do about them are business decisions. The business people must play an active role in performing the risk assessment (Step 1) and answering the upgradability question. It's their neck on the block, when your company must pay penalties or damages. The technical people assist in the risk assessment by identifying the risks, suggesting mitigation options and documenting the risk assessment. Identifying the few relevant vulnerabilities and completing the technical documentation is their domain as well.
Who does the "actual" work in the bootcamp?
You! My role is that of a teacher and facilitator. The goal of the bootcamp is that you can perform the CRA compliance of your system self-dependently.
What about an onsite bootcamp?
I can do Option 1 (risk assessement) onsite at your premises, if the traveling time is reasonable. We will agree on this before we sign the contract. You will pay the full travel costs. Options 2 and 3 are always online.
Can you cancel a bootcamp?
No, you can't. Once you have signed the contract for a bootcamp, you can't cancel it. Neither can I. However, we can postpone the bootcamp in mutual agreement.
What are the payment terms?
You will pay the full price of the ordered options in advance, before the first ordered option starts.
